A recent investigation has exposed a suspected North Korean operative attempting to infiltrate the cryptocurrency industry through freelance work. The investigation, led by cyber threat intelligence expert Heiner Garcia, involved a fake job interview that inadvertently revealed links to a broader network of North Korean threat actors. This article delves into the details of the operation, the tactics employed by the operative, and the potential implications for the crypto space.
The Setup: A Dummy Job Interview
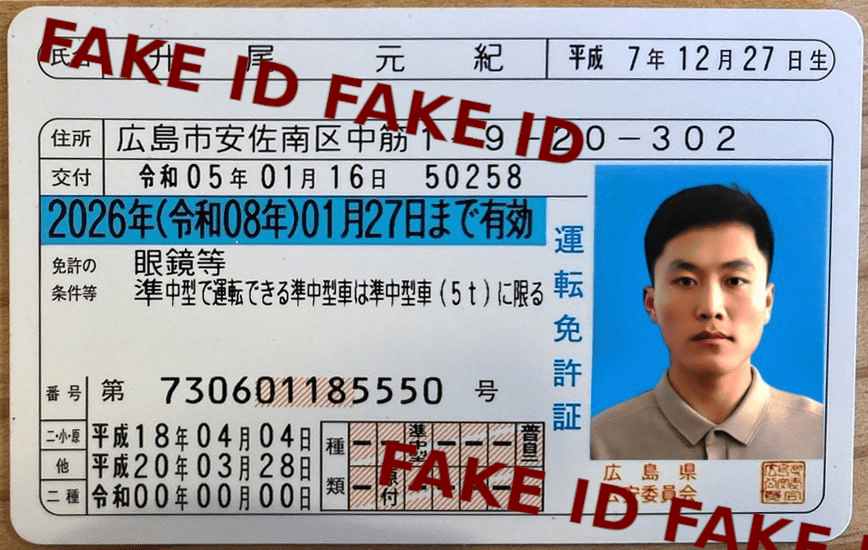
The investigation began when Garcia identified a GitHub account, “bestselection18,” suspected to be operated by an experienced North Korean IT infiltrator. This account was linked to a group attempting to secure freelance gigs on platforms like OnlyDust. Garcia’s attention was drawn to another account, “Motoki,” which, unlike most North Korean state actors, featured a human face photo.
Garcia, posing as a headhunter, contacted Motoki on Telegram and arranged a job interview for a non-existent company. Cointelegraph joined the interview to observe and potentially glean insights into the operative’s methods. The interview took place with webcams off, though Motoki had his on. During the interview, Motoki’s behavior raised red flags, including repetitive answers and an inability to speak Japanese despite claiming to be a Japanese developer.
When asked to introduce himself in Japanese, Motoki hesitated, appeared to search for a script, and ultimately rage-quit the call. This abrupt departure fueled suspicions and prompted further investigation.

Screen Sharing Slip-Up: Exposing the Network
Motoki’s sloppiness proved to be his undoing. During the interview and a previous call with Garcia, he shared his screen, inadvertently revealing access to private GitHub repositories connected to “bestselection18.” This linked Motoki to a defunct scam project and exposed the wider network.
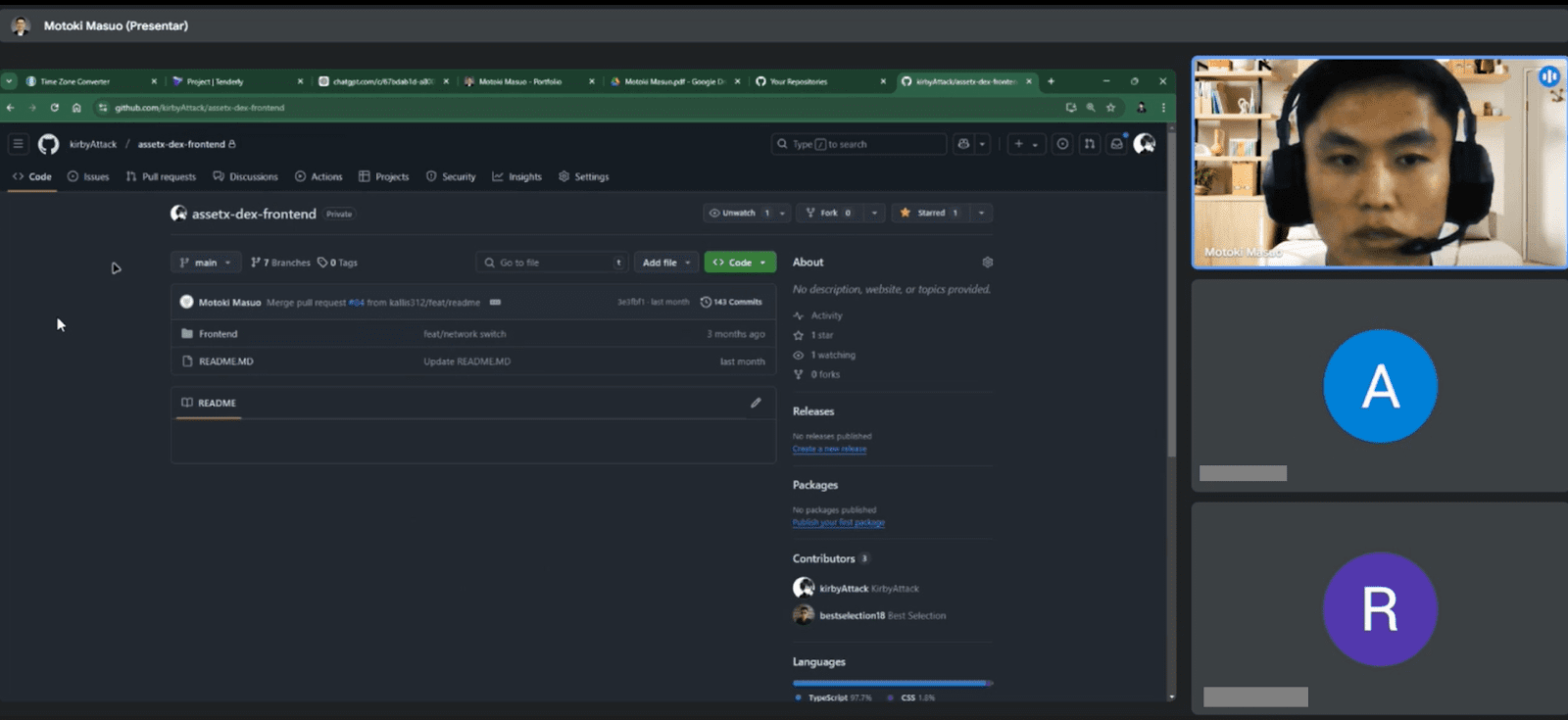
Linguistic and Behavioral Clues: Unmasking the Operative
Beyond the screen sharing blunder, several linguistic and behavioral clues pointed to Motoki’s North Korean origins. These included:
- Facial structure: Motoki’s appearance aligned more closely with the wider facial structure typically found in Korean males, as opposed to the narrower faces of Japanese males.
- Pronunciation: Motoki frequently pronounced words beginning with “r” as “l,” a common substitution among Korean speakers. He also pronounced “football” with a strong “p” sound, another characteristic of Korean-accented English.
- Lack of fluency: Claiming to be a Japanese developer, Motoki struggled with even basic Japanese phrases.
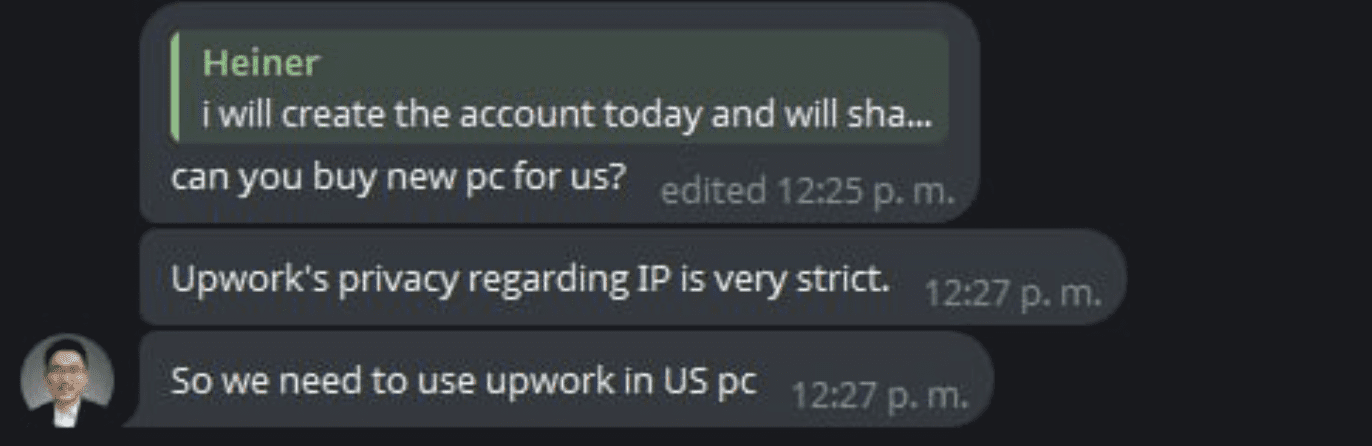
A Remote Access Scheme: Bypassing Security Measures
Following the interview, Garcia continued communicating with Motoki, pretending to be a fired headhunter seeking new opportunities. Motoki offered Garcia a deal that shed light on North Korea’s operational methods: to use Garcia’s computer. The plan involved Motoki’s handlers sending Garcia money to purchase a computer, which they would then remotely access.
This arrangement would allow the operatives to bypass VPN detection on freelancing platforms by operating from a machine in another location. This tactic highlights the lengths to which North Korean operatives will go to conceal their identities and evade security measures.
The Aftermath: Disappearance and Broader Implications
Shortly after Garcia and his partner published their findings, Motoki disappeared, scrubbing his social media profiles and online presence. This reinforces the notion that he was indeed a North Korean operative attempting to conceal his activities.
This incident is not isolated. Other reports have surfaced of North Korean cyber spies attempting to secure jobs in the tech industry, including at major crypto exchanges like Kraken. These operatives funnel their earnings back to North Korea, contributing an estimated $600 million annually to the regime’s weapons program. This underscores the urgent need for heightened vigilance and robust security measures within the cryptocurrency industry to combat this growing threat.
Key Takeaways:
- North Korean operatives are actively attempting to infiltrate the cryptocurrency industry through freelance platforms.
- They employ sophisticated tactics to conceal their identities and evade detection, including using fake identities and remote access schemes.
- Vigilance and robust security measures are crucial to protect the cryptocurrency industry from this growing threat.
- The funds generated by these operatives contribute to North Korea’s weapons program.
The “Motoki” incident serves as a stark reminder of the ongoing cyber threats facing the cryptocurrency industry and the importance of proactive measures to mitigate these risks. By understanding the tactics employed by these operatives, companies and individuals can better protect themselves from falling victim to their schemes.