What is Crocodilus Malware?
Crocodilus is a sophisticated Android malware targeting crypto wallets, designed to steal digital assets from Android devices running Android 13 or later. It uses overlays, remote access, and social engineering to compromise devices and drain crypto wallets. First identified by ThreatFabric in March 2025, Crocodilus primarily targeted users in Spain and Turkey, with potential for global expansion.
How Crocodilus Infects Android Devices
The exact infection method is unknown, but Crocodilus likely spreads through methods common to other malware:
- Fake apps: Disguised as legitimate cryptocurrency apps on the Google Play Store or third-party sites.
- SMS promotions: Suspicious text messages with malicious links.
- Malicious advertising: Infected ads on untrustworthy websites.
- Phishing attempts: Emails impersonating cryptocurrency exchanges.
Once installed, Crocodilus requests accessibility permissions, connecting to a command-and-control (C2) server. This allows attackers to display screen overlays, track keystrokes, and gain remote access.
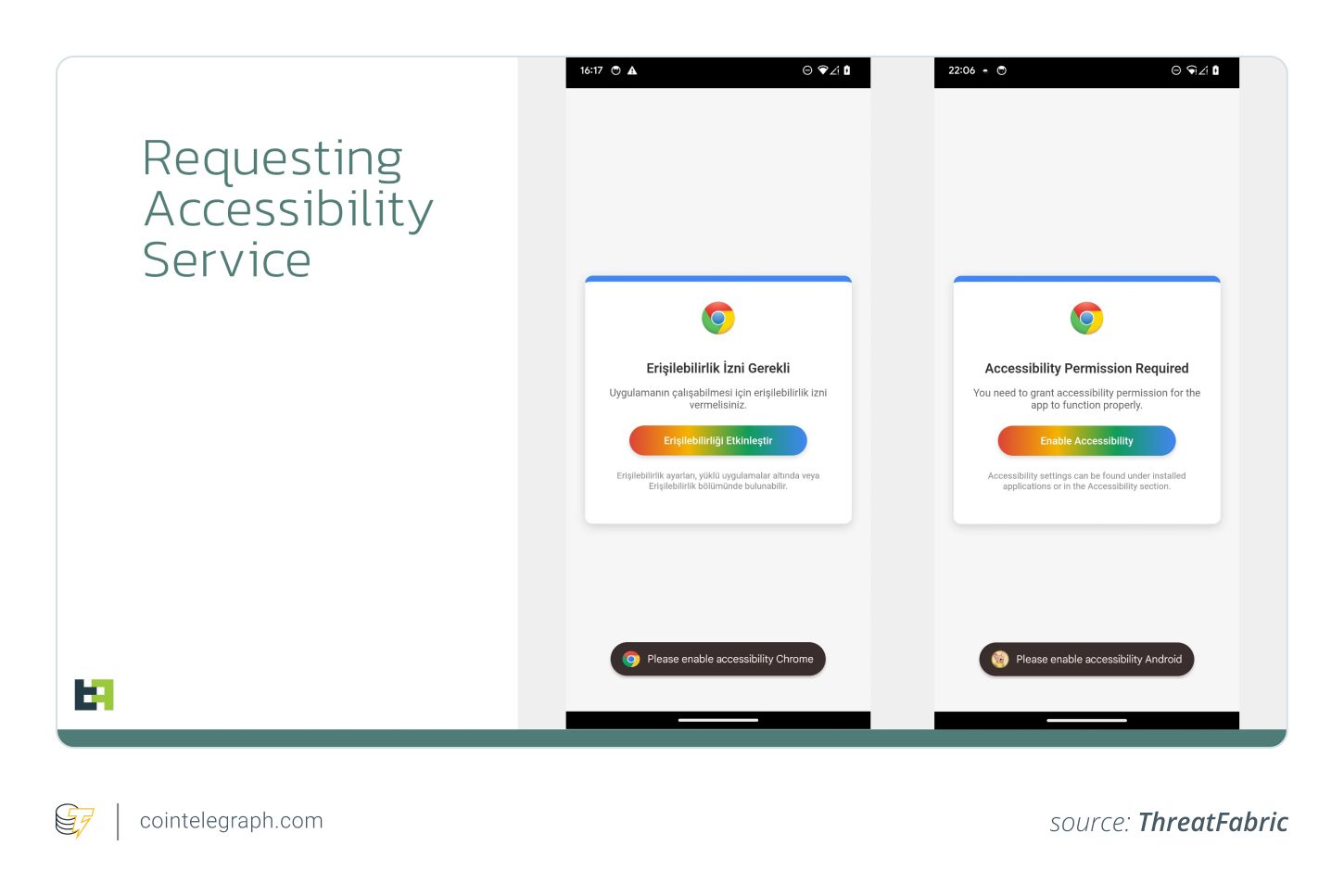
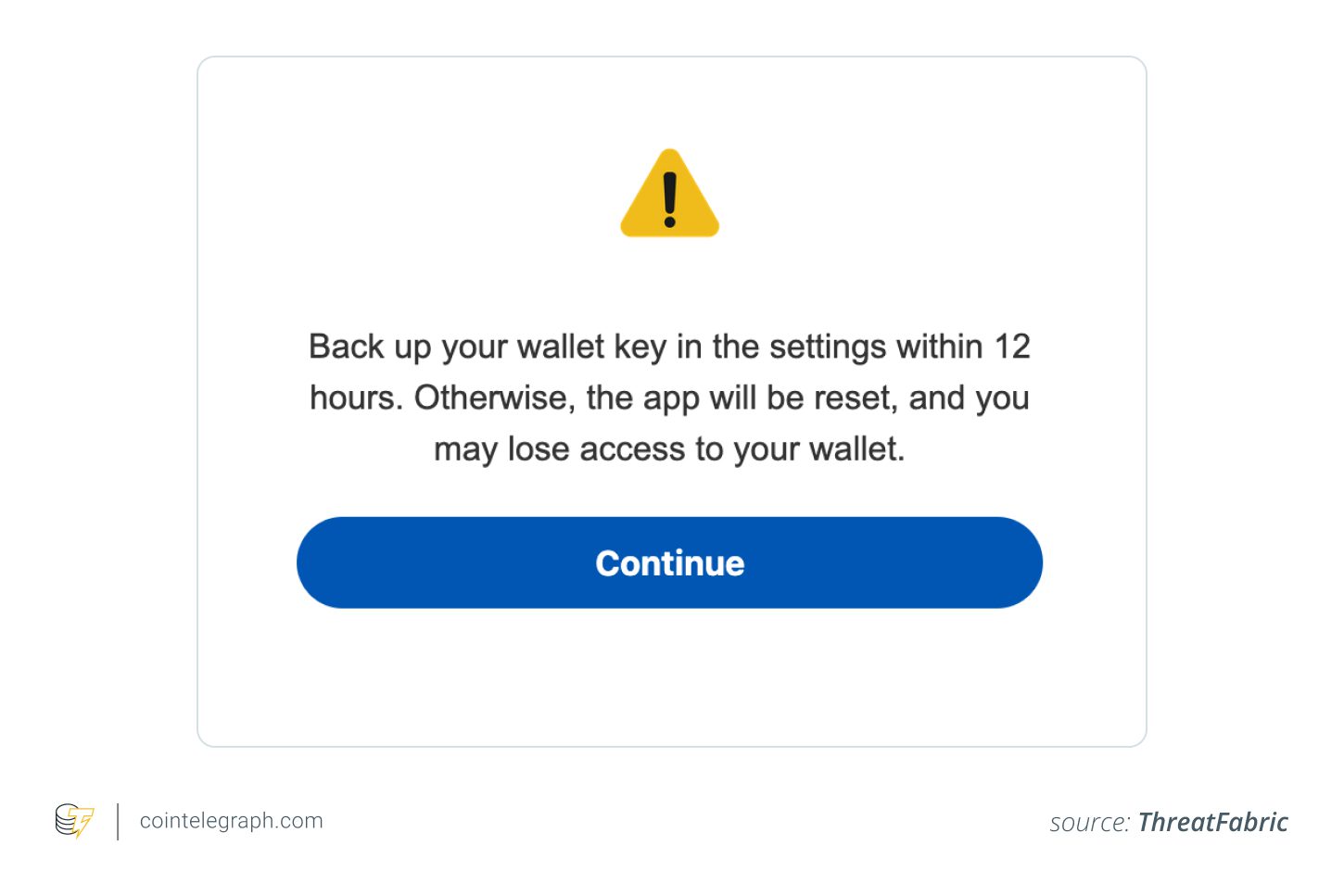
The Wallet Backup Trick
Crocodilus uses a fake overlay to trick users into revealing their seed phrase. When a user logs into their crypto wallet, the overlay appears with the message: “Back up your wallet key in the settings within 12 hours. Otherwise, the app will be reset, and you may lose access to your wallet.” Clicking “continue” prompts the user to enter their seed phrase, which is then logged and sent to the attackers.
Beyond Keylogging
Crocodilus also circumvents two-factor authentication (2FA) by recording the screen and capturing verification codes. It displays a black overlay and mutes the device to hide its activities while stealing assets in the background.
Command Capabilities
The malware supports 45 commands, including:
- SMS takeover
- Remote access
- Text modification to access private apps
What to Do If You’re a Victim of a Crocodilus Attack
Immediate action is crucial:
- Isolate your device: Disconnect from Wi-Fi/data, turn off the device, and remove the battery if possible.
- Recover assets: Use your seed phrase (stored safely) to recover your wallet on a clean device.
- Dispose of the infected device: Factory resetting may not be enough; consider a new device.
- Report the threat: Report the malicious app to relevant platforms like the Google Play Store.
How to Check for a Crocodilus Attack
Look for these telltale signs:
- Suspicious app activity: Unexplained activity in cryptocurrency or banking apps.
- Check app permissions: Review app permissions, especially accessibility permissions.
- Increased battery drain: Faster than usual battery drain.
- Data usage spikes: Sudden increases in data usage.
How to Prevent a Crocodilus Hack
Prevention is key. Protect yourself with these measures:
- Browse safely: Avoid suspicious websites.
- Use a hardware wallet: Keep your cryptocurrencies in a hardware wallet to limit the malware’s reach.
- Triple-check app downloads: Download apps only from official sources.
- Check official sources: Stay informed about Crocodilus protection methods.
Understanding Android Malware Threats in 2025
Crocodilus malware represents a significant threat to Android users involved with cryptocurrencies in 2025. As digital finance becomes increasingly prevalent, cybercriminals are developing sophisticated methods to steal digital assets. Staying informed and adopting proactive security measures is essential for safeguarding your investments.
The Evolution of Crypto Malware
Crypto malware is continuously evolving. Early forms of crypto malware primarily focused on directly stealing private keys from infected computers. Today, malware like Crocodilus employs more complex strategies such as overlay attacks and remote access to gain complete control over devices.
The Role of Social Engineering
Social engineering plays a crucial role in the success of Crocodilus and similar malware. By creating convincing fake overlays and using fear tactics, attackers trick users into willingly providing their seed phrases. Education and awareness are key to combating these techniques.
Future Trends in Crypto Malware
Experts predict that crypto malware will continue to evolve, becoming more sophisticated and difficult to detect. Zero-click attacks, which require no user interaction, are expected to become more prevalent. Additionally, malware targeting specific vulnerabilities in hardware and software will likely emerge.
The Importance of Regular Security Audits
Conducting regular security audits of your devices and applications can help identify potential vulnerabilities and prevent malware infections. Regularly reviewing app permissions and monitoring for suspicious activity are essential steps in maintaining a secure digital environment.
Staying Updated on the Latest Threats
Keeping informed about the latest crypto malware threats is crucial for protecting your digital assets. Follow reputable cybersecurity websites, blogs, and social media accounts to stay updated on emerging threats and best practices for prevention.
The Importance of Multi-Factor Authentication
While Crocodilus attempts to circumvent two-factor authentication (2FA), it remains an important security measure. Using a strong password and enabling 2FA on all your cryptocurrency accounts can significantly reduce the risk of unauthorized access.
Protecting Your Seed Phrase
Your seed phrase is the key to your cryptocurrency wallet. Storing it securely offline, in a safe physical location, is essential. Never share your seed phrase with anyone or enter it on any website or application that you do not trust.
Considering Decentralized Security Solutions
Decentralized security solutions, such as multi-signature wallets and decentralized identity management systems, can provide additional layers of protection for your cryptocurrency assets. These solutions distribute control over your assets, making it more difficult for attackers to compromise your wallet.
Educating Others
Sharing your knowledge about crypto malware and security best practices with others can help create a more secure digital environment for everyone. Encourage your friends and family to stay informed and adopt proactive security measures to protect their cryptocurrency assets.