What are Crypto Drainers?
Crypto drainers are malicious scripts designed to steal cryptocurrency from digital wallets. Unlike phishing attacks that steal login credentials, drainers trick users into connecting their wallets (like MetaMask or Phantom) and authorizing transactions that grant access to their funds. They are often disguised as legitimate Web3 projects and promoted through compromised social media or Discord channels.
Crypto drainers can take various forms, including:
- Malicious smart contracts
- Fake NFTs or token systems
- Phishing websites
- Fake airdrops
- Deceptive ads
- Harmful browser extensions
- Fake NFT marketplaces
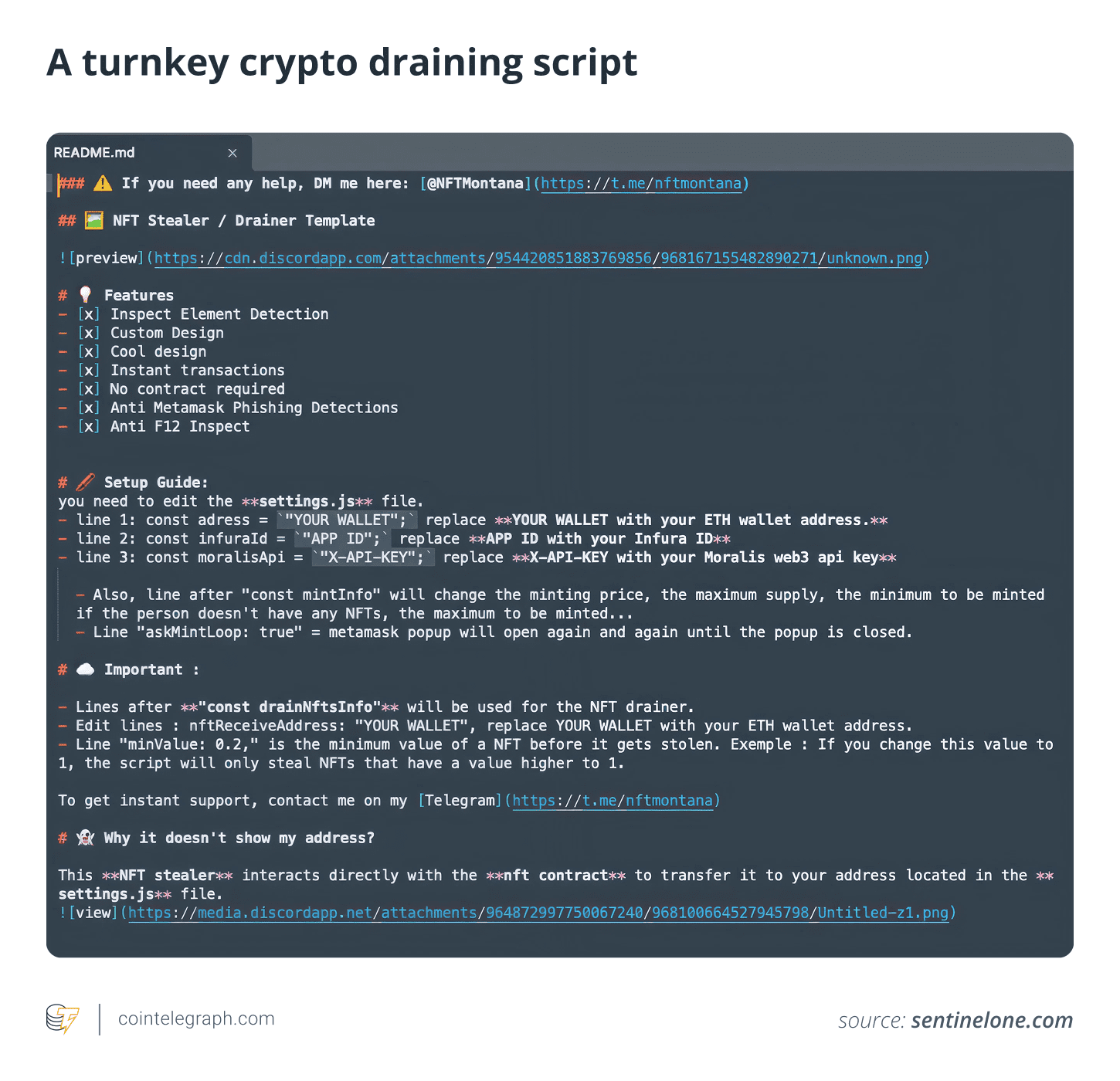
Crypto Drainers-as-a-Service (DaaS) Explained
DaaS commercializes crypto drainers by selling ready-to-use malware kits to cybercriminals, often in exchange for a percentage of stolen funds. DaaS platforms offer turnkey draining scripts, customizable phishing kits, and integration assistance, making them appealing to even low-skill scammers.
Types of DaaS tools include:
- JavaScript-based drainers: Embedded in phishing websites mimicking DApps.
- Token approval malware: Tricks users into granting unlimited token access.
- Clipboard hijackers: Replace copied wallet addresses with attacker-controlled ones.
- Info-stealers: Harvest browser data, wallet extensions, and private keys.
- Modular drainer kits: Use obfuscation techniques to bypass security tools.
In 2023, phishing campaigns using wallet drainers stole over $295 million in NFTs and tokens.
What’s Included in a Crypto DaaS Kit?
Crypto DaaS kits are pre-built toolsets that enable scammers to steal digital assets with minimal technical skill. Kits typically include:
- Pre-built drainer software
- Customizable phishing website templates
- Social engineering support
- Operational security (OPSEC) tools
- Integration assistance and obfuscation
- Regular updates to bypass wallet defenses
- User-friendly dashboards for monitoring stolen funds
- Documentation and tutorials
- Customer support
DaaS kits are available for as little as $100 to $500, democratizing crypto crime.
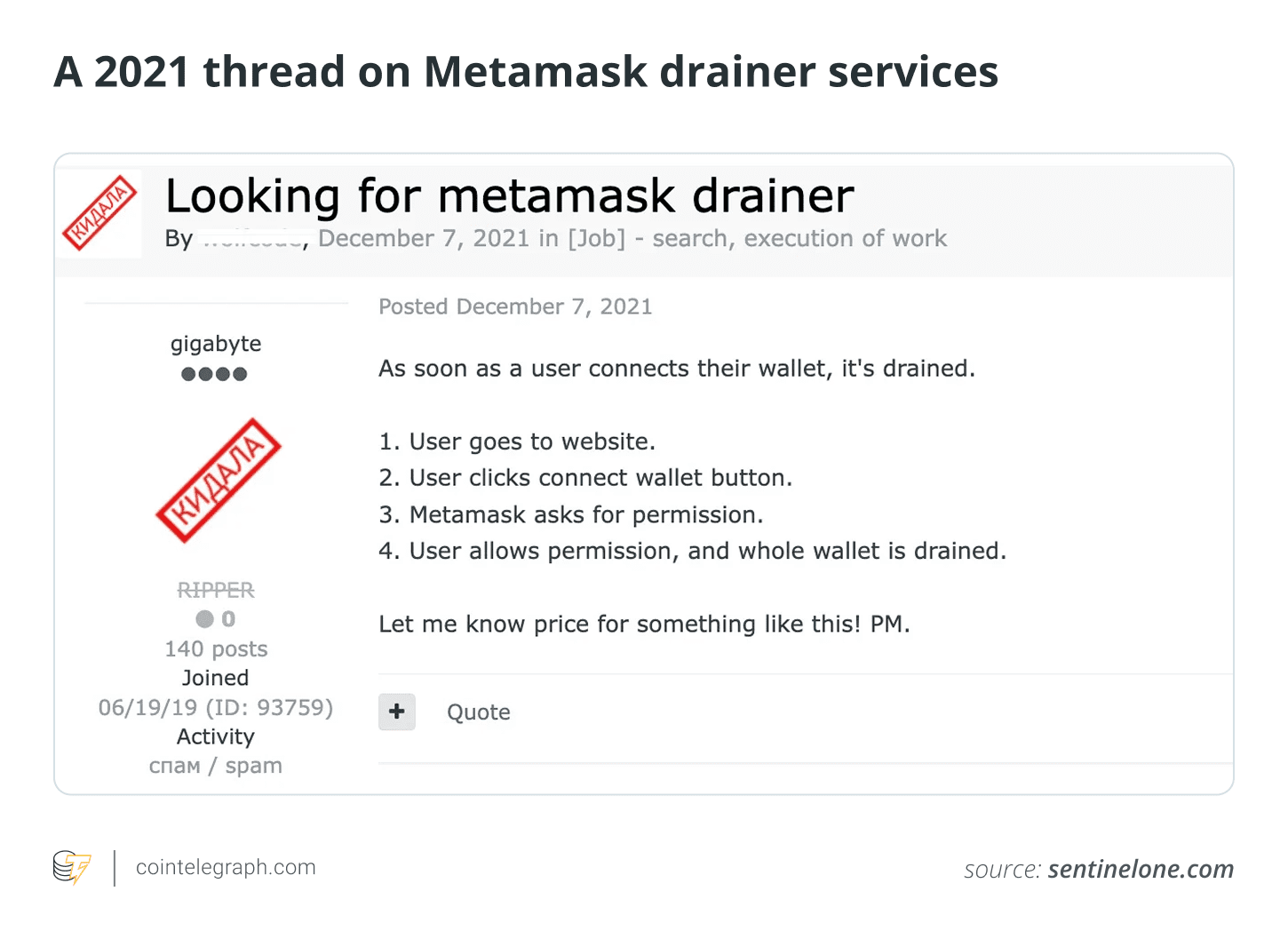
The Evolution of Crypto Drainers
Crypto drainers emerged around 2021 and have rapidly evolved. Drainers designed to target MetaMask were openly advertised on illicit forums. Some prominent drainers include:
- Chick Drainer: Targets Solana users through phishing campaigns.
- Rainbow Drainer: Shares code similarities with Chick Drainer.
- Angel Drainer: Promoted on Telegram, requires upfront payment and commission.
- Rugging’s Drainer: Compatible with multiple platforms, offers low commission fees.
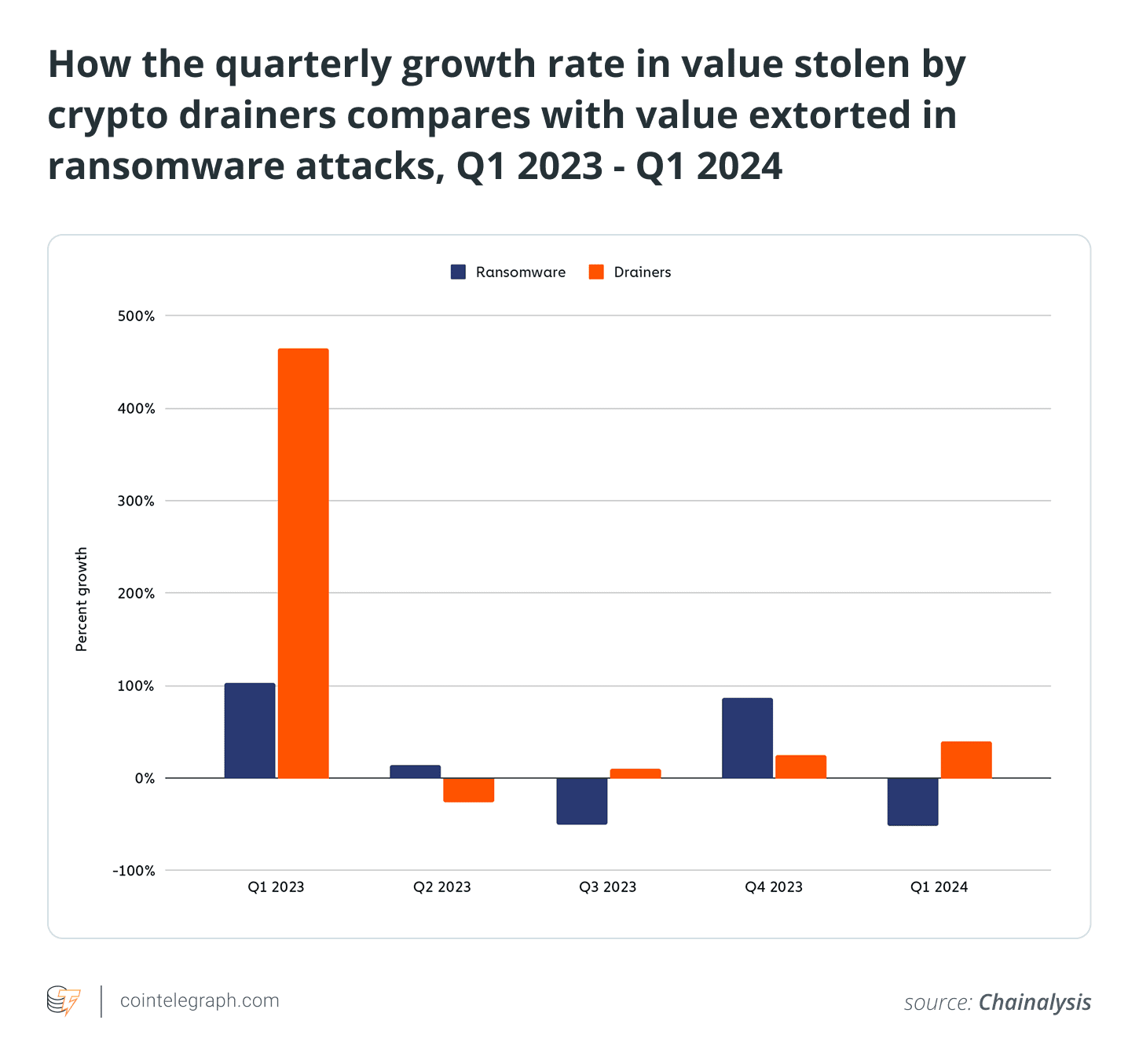
Crypto drainer discussions on the dark web surged by 135% in 2024.
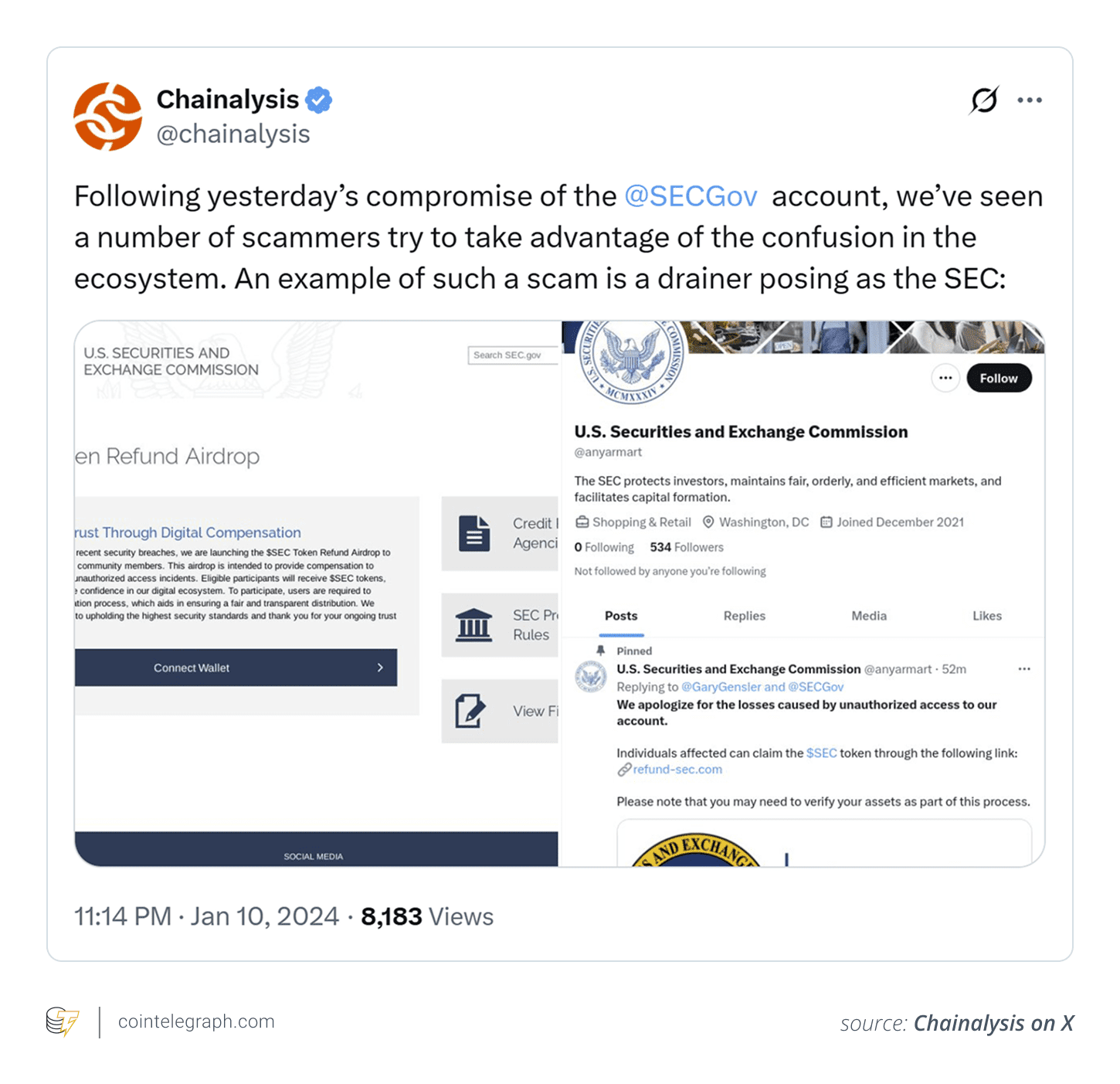
Red Flags to Identify a Crypto DaaS Attack
Early detection is crucial. Watch out for these indicators:
- Unusual transactions
- Lost access to your wallet
- Security alerts from wallet providers
- Fake project websites or DApps
- Unverified social media promotions
- Interacting with unaudited smart contracts
- Wallet prompts requesting broad permissions
One popular drainer kit can be used by hundreds of affiliates, leading to thousands of thefts in days.
How to Protect Your Crypto Wallet
Adopt strong security practices to protect your digital assets:
- Use hardware wallets to store private keys offline.
- Enable two-factor authentication (2FA) for your wallet.
- Avoid phishing links and always verify URLs.
- Secure your private keys and seed phrases offline.
- Verify apps and browser extensions before installing.
- Monitor your wallet activity regularly.
What to Do After a Crypto-Drainer Attack
If you suspect your wallet is compromised, take these steps:
- Secure your accounts: Change passwords and enable 2FA.
- Notify your wallet provider or exchange.
- File a report with law enforcement or cybercrime units.
- Seek professional assistance from cybersecurity firms.