The aftermath of the Coinbase data breach continues to unfold, with the perpetrator now taunting blockchain investigator ZachXBT. This incident sheds light on the complexities of cryptocurrency security, the use of decentralized exchanges like THORChain for illicit activities, and the growing legal challenges facing Coinbase.
The Onchain Taunt
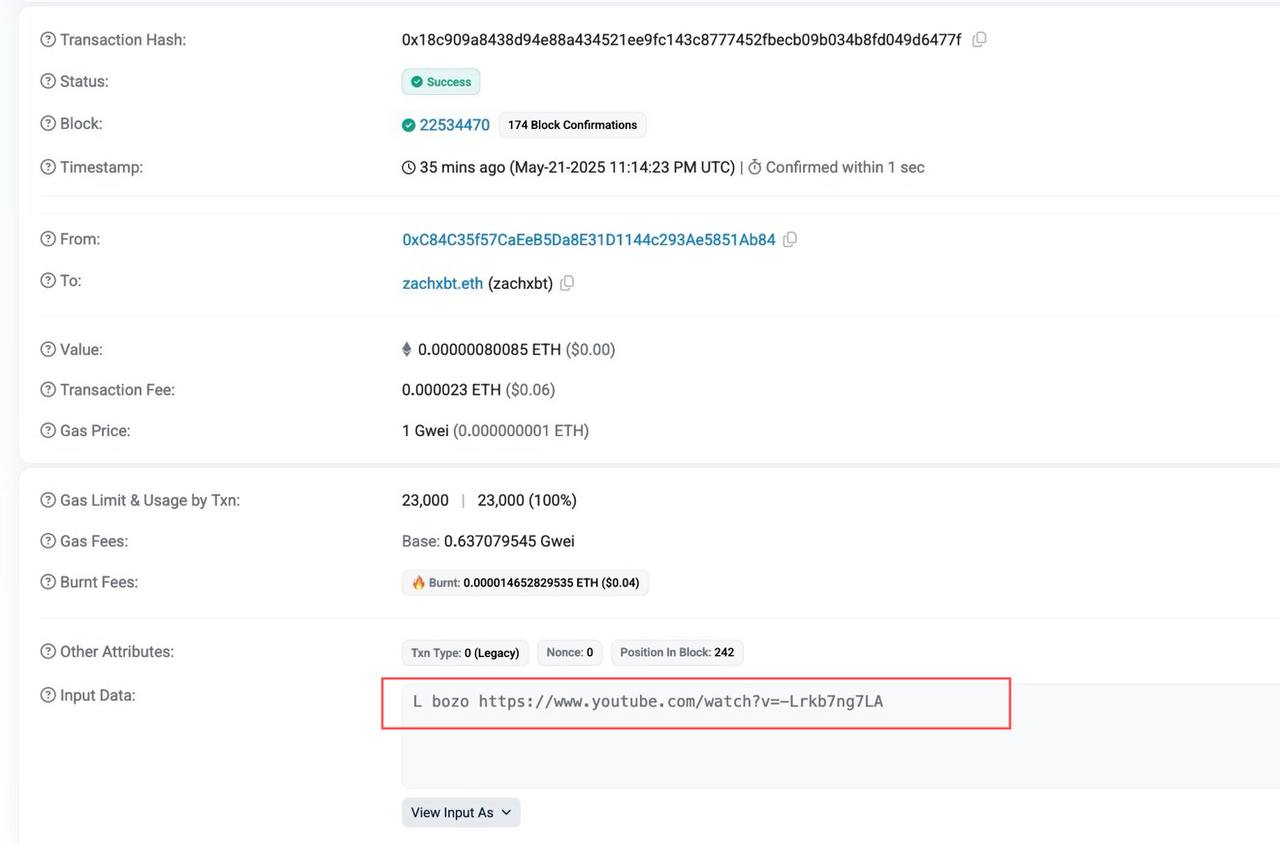
On May 21, the hacker, responsible for compromising the data of tens of thousands of Coinbase users, executed a transaction on the Ethereum blockchain. Using the input data field, the hacker sent a direct message to ZachXBT, a well-known figure in the crypto space for his investigative work. The message, a dismissive “l bozo,” accompanied by a meme video of NBA player James Worthy, was a clear attempt to mock ZachXBT’s efforts to track and expose the hacker’s activities. This bold move highlights the brazen attitude of the hacker and their willingness to engage publicly, even after committing a significant data breach.
The $42.5 Million THORChain Swap
The taunt followed a substantial cryptocurrency swap executed by the hacker through THORChain, a decentralized cross-chain liquidity protocol. The hacker converted approximately $42.5 million worth of Bitcoin (BTC) into Ether (ETH). This transaction is significant for several reasons:
- Scale: The sheer size of the swap demonstrates the hacker’s access to a considerable amount of stolen funds.
- THORChain Usage: The choice of THORChain raises concerns about the protocol’s potential for facilitating money laundering.
- Cross-Chain Conversion: The conversion from BTC to ETH complicates tracking efforts, as it moves the funds across different blockchains.
ZachXBT was quick to flag the onchain message, linking it directly to the Coinbase data breach that impacted at least 69,400 users. This rapid response underscores the importance of blockchain analytics in identifying and tracking illicit activities within the cryptocurrency ecosystem.
Further Fund Movements
The hacker’s activity didn’t stop with the initial swap. Blockchain security firm PeckShield reported that the hacker continued to move funds, exchanging 8,697 ETH for 22 million Dai (DAI). A closely linked address, having received 9,081 ETH via THORChain, also converted its holdings into 23 million DAI. This continuous movement and conversion of funds make it increasingly challenging for law enforcement to trace and recover the stolen assets.
Coinbase Lawsuits and Fallout
The Coinbase data breach has triggered a series of legal challenges for the company. At least six lawsuits have been filed, alleging that Coinbase failed to implement adequate security measures to protect user data and mishandled the response to the breach. Plaintiffs argue that the stolen data, including names, home addresses, and other personal information, puts users at risk of identity theft and other forms of financial harm.
Coinbase estimates the potential financial impact of the breach to be between $180 million and $400 million, encompassing remediation costs and customer compensation. The company initially offered a $20 million bounty for information leading to the identification of the hackers, signaling the severity of the situation and the company’s commitment to addressing the breach.
THORChain’s Role and Controversy
The use of THORChain by the Coinbase hacker has amplified concerns about the protocol’s potential for illicit use. THORChain, designed to facilitate cross-chain swaps without the need for centralized intermediaries, has faced scrutiny for its role in enabling money laundering activities. This is due to the pseudo-anonymous nature of cryptocurrency transactions and the ability to easily move funds across different blockchains.
In March, THORChain experienced a surge in swap volume following the $1.4 billion Bybit hack. Blockchain security firms identified North Korea’s Lazarus Group as a potential user of THORChain to launder stolen funds. This incident, coupled with the Coinbase hacker’s actions, has placed significant pressure on THORChain to implement stricter measures to prevent illicit activities on its platform.
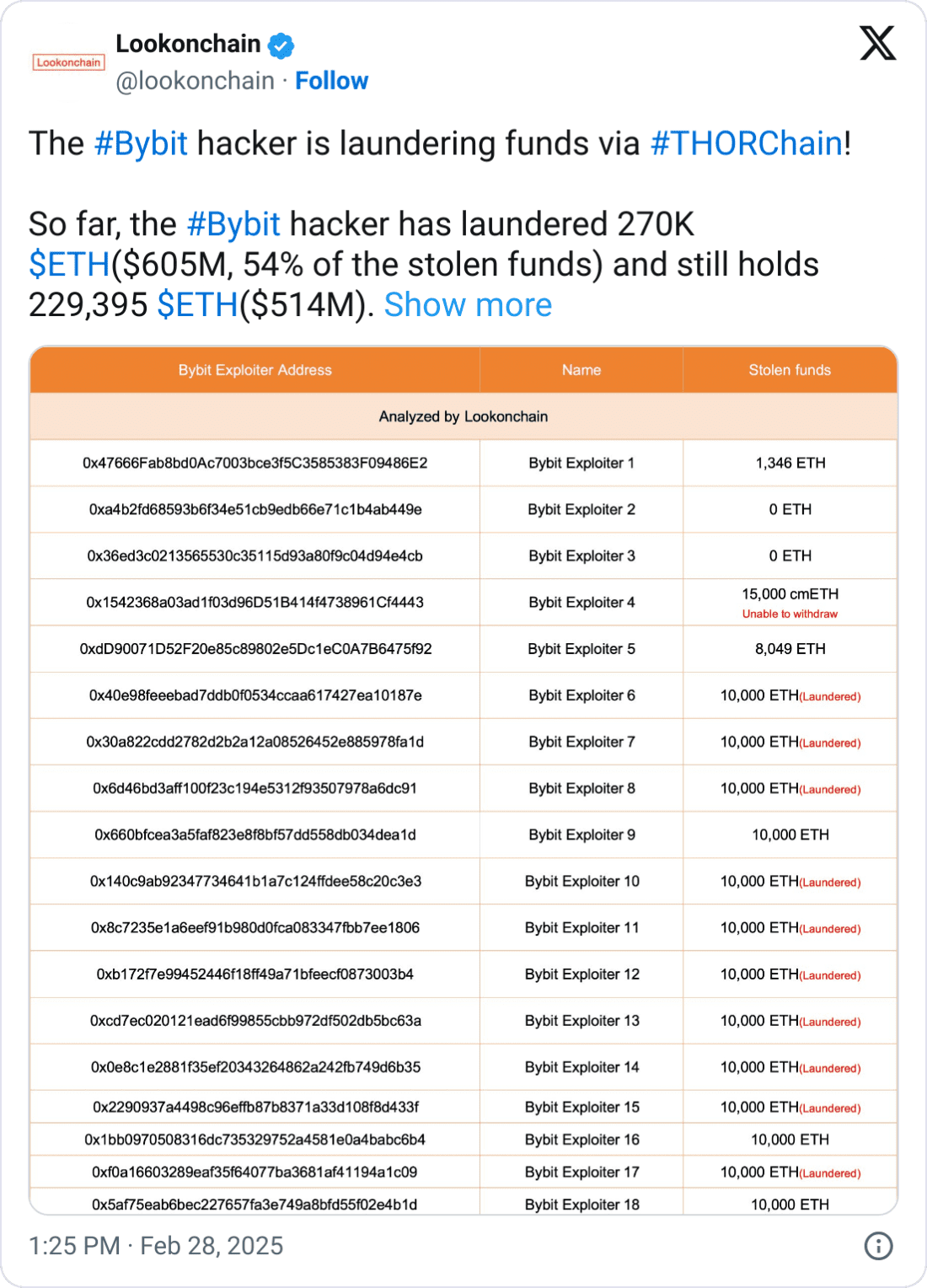
The controversy surrounding THORChain intensified when a developer, known as “Pluto,” resigned after a vote to block transactions linked to Lazarus failed. This internal conflict highlights the challenges THORChain faces in balancing its commitment to decentralization with the need to prevent illicit activities.
Key Takeaways
- The Coinbase data breach has had significant repercussions, leading to lawsuits and reputational damage.
- The hacker’s use of THORChain raises concerns about the protocol’s role in facilitating money laundering.
- Blockchain analytics and security firms play a crucial role in tracking illicit cryptocurrency transactions.
- Cryptocurrency exchanges and protocols must prioritize security measures to protect user data and prevent illicit activities.
The Coinbase hacker’s taunt and the subsequent scrutiny of THORChain underscore the ongoing challenges in the cryptocurrency space related to security, regulation, and the prevention of illicit activities. As the industry matures, it is essential for exchanges, protocols, and law enforcement agencies to collaborate to create a safer and more secure environment for all users.