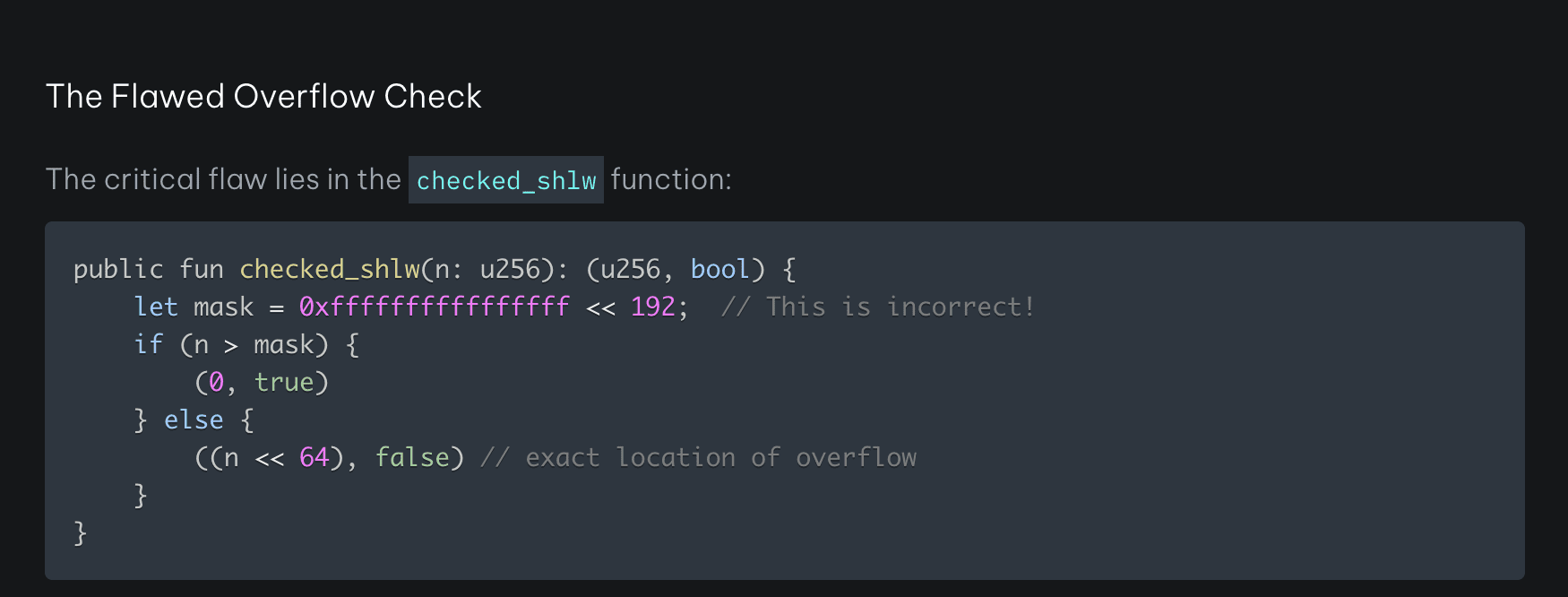
Blockchain security firm Dedaub has released a comprehensive post-mortem report detailing the Cetus decentralized exchange (DEX) hack. The report identifies a flaw in the Cetus automated market maker (AMM) liquidity parameter check as the root cause, revealing vulnerabilities in code designed to prevent overflows.
According to Dedaub’s analysis, the hackers exploited a weakness in the most significant bits (MSB) check. This allowed them to manipulate liquidity parameters drastically, enabling them to establish significant positions with minimal input. The result was a catastrophic draining of liquidity pools containing hundreds of millions of dollars worth of tokens. The Dedaub researchers explained, “This allowed them to add massive liquidity positions with just one unit of token input, subsequently draining pools collectively containing hundreds of millions of dollars worth of tokens.”
This incident underscores the growing need for robust cybersecurity measures within the cryptocurrency and Web3 space. The increasing frequency and sophistication of cyberattacks targeting digital assets highlight the vulnerabilities inherent in decentralized finance (DeFi) platforms. The Cetus hack and Dedaub’s analysis offer crucial lessons for developers and security professionals alike, emphasizing the importance of rigorous code auditing and robust overflow protection mechanisms.
Cetus Hack: A Timeline and Breakdown
- May 22, 2024: The Cetus DEX, built on the Sui network, was targeted in a sophisticated cyberattack.
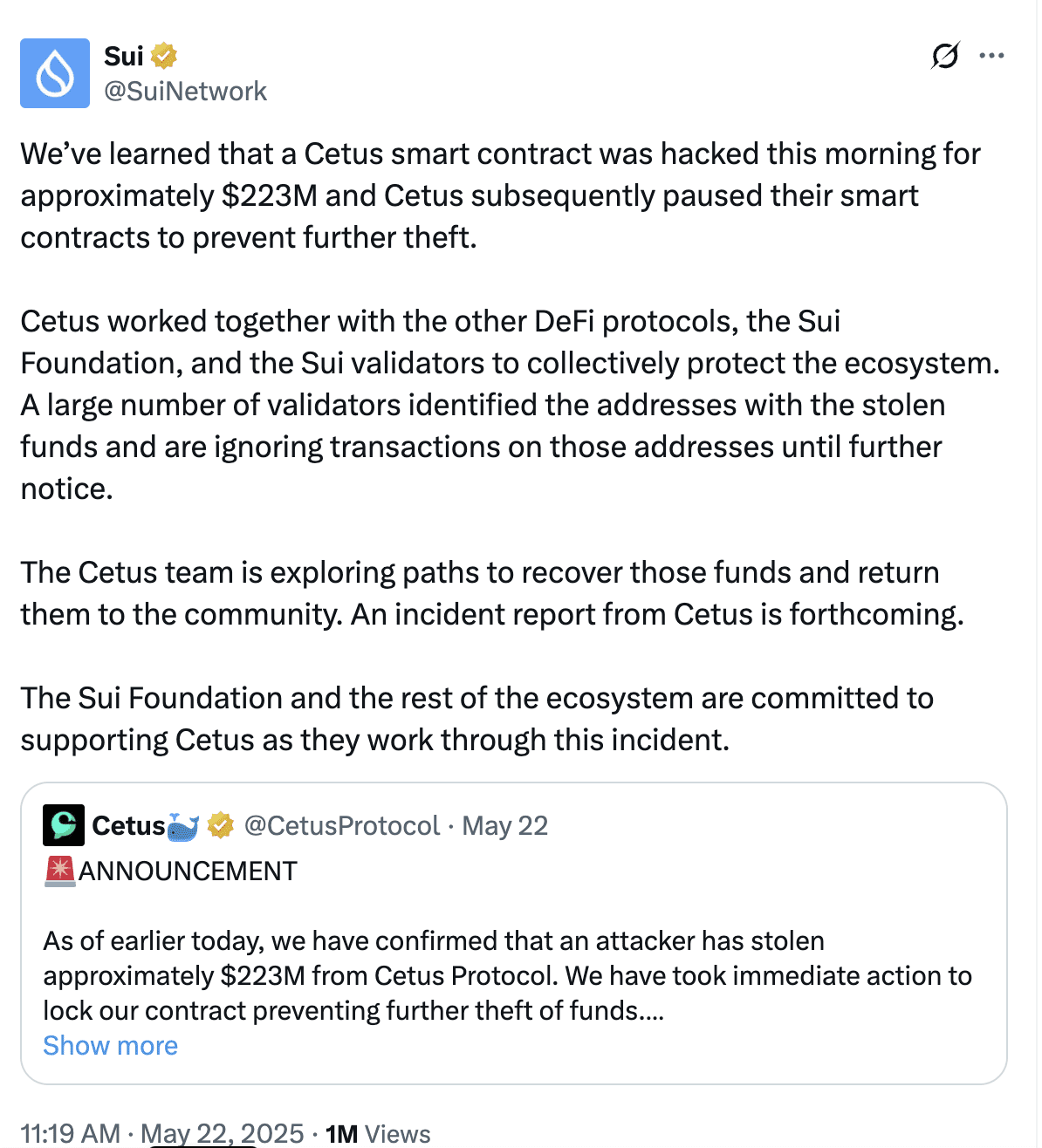
- $223 Million Loss: Within 24 hours, the hack resulted in a staggering $223 million loss of user funds.
- Immediate Response: The Cetus team and the Sui Foundation acted swiftly, collaborating with Sui network validators to freeze the majority ($163 million) of the stolen assets.
- Dedaub’s Investigation: The blockchain security firm Dedaub conducted a thorough post-mortem analysis to pinpoint the vulnerability exploited by the hackers.
The Technical Details: MSB Check and Liquidity Manipulation
The Dedaub report highlights the critical role of the flawed MSB check in enabling the exploit. Here’s a simplified explanation:
- Liquidity Parameters: AMMs like Cetus rely on specific parameters to manage liquidity within trading pools.
- Overflow Protection: Code includes “overflow” checks to prevent values from exceeding defined limits, ensuring the integrity of calculations.
- MSB Check Flaw: The vulnerability resided in the implementation of the MSB check, failing to adequately prevent manipulation of liquidity parameters.
- Exploitation: Hackers leveraged this flaw to artificially inflate liquidity positions using only a small amount of input tokens.
- Draining the Pools: This allowed them to subsequently drain the pools, extracting massive amounts of tokens.
Centralization Debate: Freezing Stolen Funds
The decision by Sui network validators to freeze the majority of the stolen funds sparked heated debate within the crypto community. While many praised the swift action to recover assets, others raised concerns about the implications for decentralization.
Arguments Against the Freeze:
- Censorship: Critics argued that freezing transactions represents a form of censorship, undermining the fundamental principles of blockchain technology.
- Centralized Control: Some view the validators’ intervention as evidence of centralized control over the Sui network, contradicting the ethos of DeFi.
- Permissioned Database: Concerns were raised that such actions transform the blockchain into a permissioned database, eroding its trustless nature.
Arguments For the Freeze:
- Asset Recovery: Supporters emphasized the importance of recovering stolen assets for affected users.
- Preventing Further Harm: The freeze prevented the hackers from further exploiting the stolen funds.
- Protecting the Ecosystem: The action helped to protect the overall integrity of the Sui network and its ecosystem.
Lessons Learned and Future Implications
The Cetus hack serves as a stark reminder of the challenges and risks associated with DeFi. It highlights the importance of:
- Rigorous Code Auditing: Thorough audits are crucial to identify and address potential vulnerabilities before they can be exploited.
- Robust Overflow Protection: Implementing robust overflow checks is essential to prevent manipulation of liquidity parameters and other critical data.
- Community Engagement: Open communication and collaboration between developers, security researchers, and the community are vital for strengthening DeFi security.
- Decentralization vs. Security: Finding the right balance between decentralization and security remains a critical challenge for the DeFi space.
The incident also underscores the ongoing debate surrounding centralization and control within the blockchain ecosystem. As DeFi continues to evolve, it is crucial to address these concerns and develop solutions that promote both security and decentralization.