Cetus, a Sui-native decentralized exchange (DEX), experienced a significant security breach resulting in the theft of $220 million in cryptocurrency. In response, Cetus has offered a $6 million white hat bounty to the hacker in exchange for the return of the stolen assets. Concurrently, the Sui Network’s reaction to the hack, including considerations for an emergency whitelist function, has ignited discussions about the true nature of decentralization in the blockchain space.
The $220 Million Cetus Hack: A Breakdown
On May 22, Cetus was exploited, leading to a loss of over $220 million in cryptocurrency. However, swift action by Cetus and the Sui Network resulted in the freezing of $162 million of the stolen funds. The exploited assets included a substantial amount of Ether (ETH).
Cetus’ $6 Million White Hat Bounty
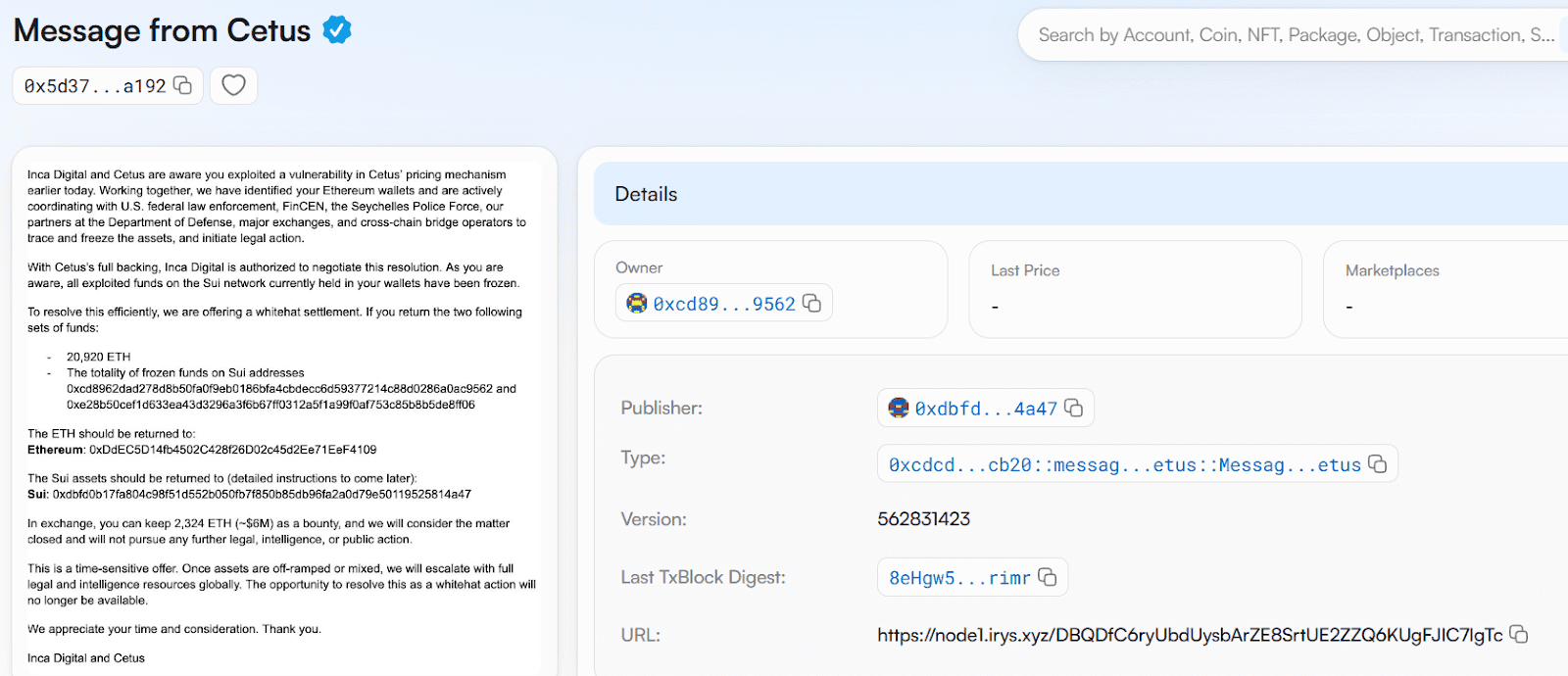
To incentivize the return of the remaining stolen funds, Cetus has publicly offered a white hat bounty of up to $6 million. The offer, embedded in a blockchain transaction, states that the hacker can retain 2,324 ETH (approximately $6 million) if all stolen funds, currently frozen on the Sui blockchain, are returned. Cetus has warned that failure to return the assets or attempts to move them to cryptocurrency mixers will result in full legal and intelligence action.
Sui Network’s Response and Decentralization Debate
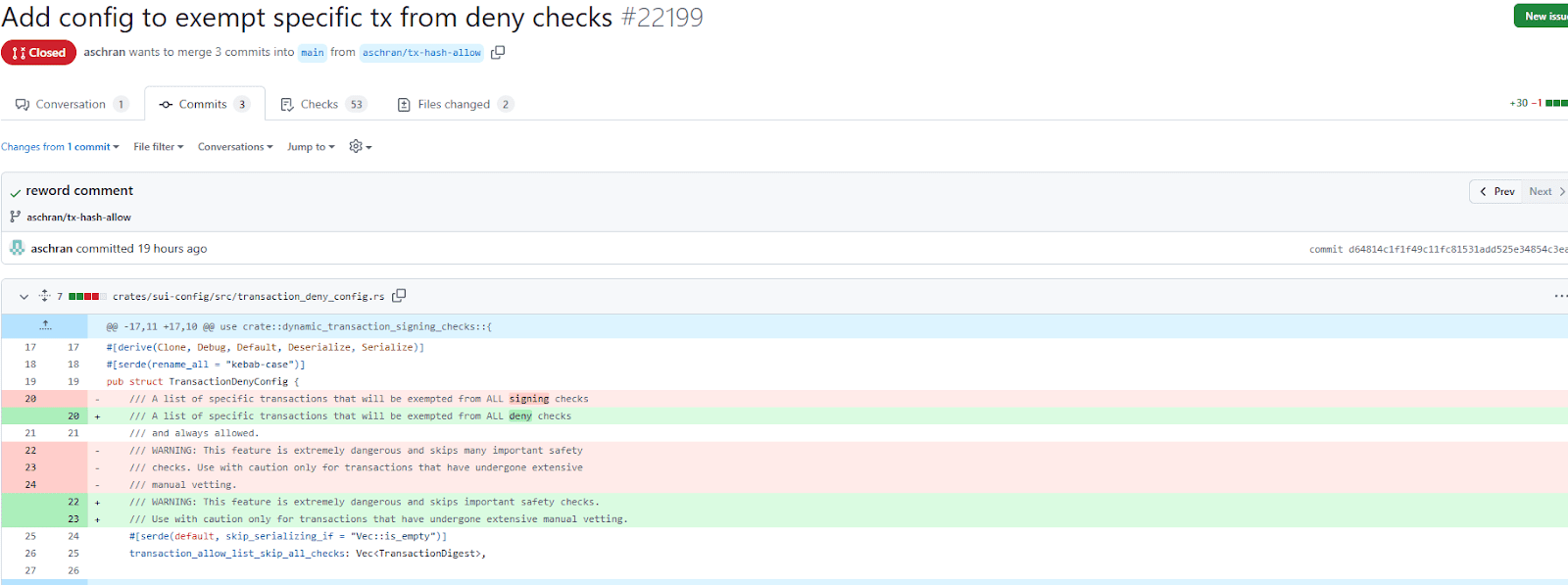
The Sui Network’s response to the Cetus hack has triggered a heated debate about decentralization. Specifically, the consideration of an emergency whitelist function that would override standard security checks to recover the stolen funds has raised concerns. GitHub activity reveals that the Sui team considered implementing this function, allowing specific transactions to bypass normal protocols.
The proposed whitelist function sparked criticism from some members of the crypto community, who argued that such actions undermine the core principles of a decentralized, permissionless network. Critics claim that the ability to unilaterally override transactions contradicts the promise of immutability and censorship resistance.
However, others view the rapid response by the Sui team as a positive development, demonstrating the network’s ability to react effectively to security threats. Supporters argue that true decentralization involves not only distributed control but also the capacity to act in the best interests of the community. Some argue that the ability to intervene in exceptional circumstances, such as a large-scale hack, is a sign of a mature and responsive decentralized system.
Broader Context: Cryptocurrency Hacks on the Rise
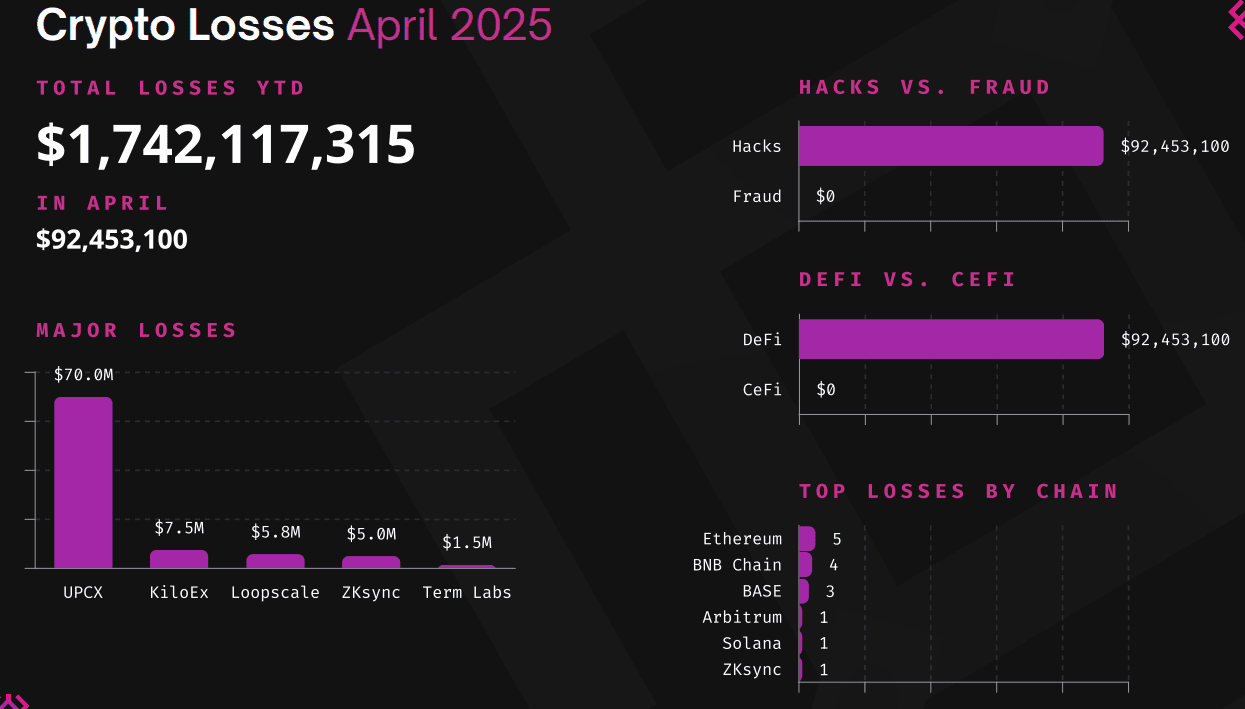
The Cetus hack is part of a broader trend of increasing cryptocurrency-related exploits. Recent data indicates a significant surge in cryptocurrency hacks, with $90 million stolen across 15 incidents in April, representing a 124% increase compared to March. Earlier this year, the Bybit exchange suffered a massive $1.4 billion loss due to a security breach. These incidents underscore the ongoing challenges in securing digital assets and the importance of robust security measures.
White Hat Bounties: A Growing Trend
The use of white hat bounties, like the one offered by Cetus, is becoming increasingly common in the cryptocurrency industry. These bounties incentivize ethical hackers to identify and report vulnerabilities, helping to prevent future exploits. A previous example includes a bounty offered after the Ronin Network exploit. The logic is that it can cost significantly less to pay for a white hat bounty than to recoup losses of a security breach. These programs play a crucial role in enhancing the security and resilience of blockchain networks.
Looking Ahead
The Cetus hack and the subsequent debate surrounding Sui Network’s response highlight the complex challenges facing the decentralized finance (DeFi) ecosystem. Balancing the principles of decentralization with the need for security and responsiveness is an ongoing process. The outcome of Cetus’ bounty offer and the future development of Sui’s governance mechanisms will be closely watched by the crypto community.