Despite significant losses from crypto hacks, including the $1.4 billion Bybit incident, Hacken CEO Dyma Budorin asserts that the crypto industry’s approach to security hasn’t evolved sufficiently. In an interview, Budorin highlighted the over-reliance on limited measures like bug bounties and penetration tests, urging companies to adopt more comprehensive security strategies mirroring those of traditional industries.
This article delves into the shortcomings of current crypto security practices and explores the need for a paradigm shift towards layered defenses. We’ll examine Budorin’s recommendations, the improvements in post-hack responses, and the broader context of rising crypto losses due to security breaches.
The Problem: Inadequate Crypto Security Measures
Budorin argues that the prevailing ‘pentest and bug bounty’ approach is insufficient. He contends that crypto companies need to implement a multi-faceted approach encompassing:
- Supply-Chain Security: Securing the software and hardware components used in crypto operations.
- Operational Security: Implementing robust procedures and policies to prevent internal threats and errors.
- Blockchain-Specific Security Assessments: Tailored security reviews addressing the unique vulnerabilities of blockchain technology.
He emphasizes that these measures are standard practice in established Web2 companies, but are often overlooked in the crypto space. The lack of these robust security layers leaves crypto platforms vulnerable to a wide range of attacks.

A Glimmer of Hope: Real-Time Blacklisting
While criticizing the overall security landscape, Budorin acknowledged a positive development: faster blacklisting of stolen funds. He cited Chainalysis’s near real-time blacklisting as a significant improvement over the previous three-day delay, which allowed hackers ample time to launder stolen assets.
However, he tempered this optimism, stating that while faster blacklisting helps, it doesn’t address the underlying systemic issues in crypto security practices. A reactive measure, while important, cannot replace proactive, layered security.
The Bybit Hack: A Case Study in Vulnerability
The $1.4 billion Bybit hack serves as a stark example of the vulnerabilities plaguing the crypto space. The exploit of a safe wallet vulnerability resulted in the largest crypto hack in history, with the stolen funds laundered within just 10 days. This incident underscores the urgency for enhanced security measures and a more proactive approach to threat detection and prevention.
April 2025: A Month of Soaring Losses
Data from PeckShield indicates that April 2025 saw a staggering $360 million in digital assets stolen across 18 hacking incidents. This represents a 990% increase compared to March’s losses of approximately $33 million. A significant portion of these losses stemmed from an unauthorized Bitcoin transfer, highlighting the diverse attack vectors targeting crypto assets.
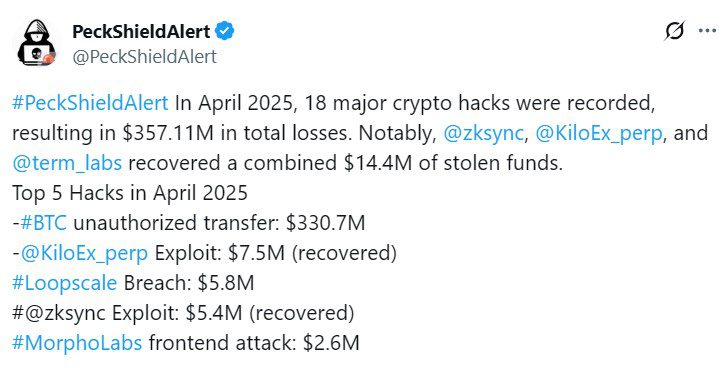
The $330 Million Bitcoin Theft: Social Engineering on the Rise
Blockchain investigator ZachXBT flagged a suspicious $330 million BTC transfer, later confirming it was a social engineering attack targeting an elderly individual in the United States. This incident shines a light on the growing trend of social engineering attacks, which exploit human vulnerabilities to gain access to crypto assets. Educating users about phishing scams and other social engineering tactics is crucial in mitigating this risk.
Key Takeaways & Recommendations
- Layered Security is Essential: Crypto companies must move beyond basic security measures and adopt comprehensive, layered strategies.
- Proactive vs. Reactive: While post-hack responses are improving, proactive security measures are paramount.
- Address Supply Chain Risks: Secure the software and hardware components used in crypto operations.
- Improve Operational Security: Implement robust procedures to prevent internal threats and human error.
- User Education: Educate users about phishing scams, social engineering, and other security threats.
In conclusion, the crypto industry must prioritize security and implement robust, multi-layered defenses to protect against increasingly sophisticated attacks. The current reliance on limited security measures is simply not sufficient in the face of escalating threats. A paradigm shift towards a more proactive and comprehensive approach is essential to safeguard the future of crypto.