The Instagram account of the popular hip-hop group Migos was recently hacked, with the attacker using the platform to target Raj Gokal, the co-founder of Solana, in an apparent blackmail scheme. This incident highlights growing concerns around social media security, cryptocurrency vulnerabilities, and the potential misuse of personal data.
The Hack and Ransom Demands:
On May 27th, the Migos’ official Instagram account was breached, and the hacker posted several images, including what appeared to be Gokal holding his passport and driver’s license. These images contained sensitive personal information, including his full name, date of birth, and address. The hacker then tagged Gokal and included captions demanding 40 Bitcoin as ransom, indicating a failed extortion attempt. Other images included what was claimed to be Gokal’s wife holding her driver’s license, along with a dump of contact information such as phone numbers and email addresses.
The Significance of Identity Document Photos:
The type of photos posted are often associated with Know Your Customer (KYC) verification processes used by cryptocurrency exchanges. These processes require users to provide identification documents to comply with regulations and prevent illicit activities. The source of these photos and how they ended up in the hacker’s possession remain unknown, raising questions about potential data breaches or security vulnerabilities within the crypto ecosystem.
Solana and Gokal’s Response:
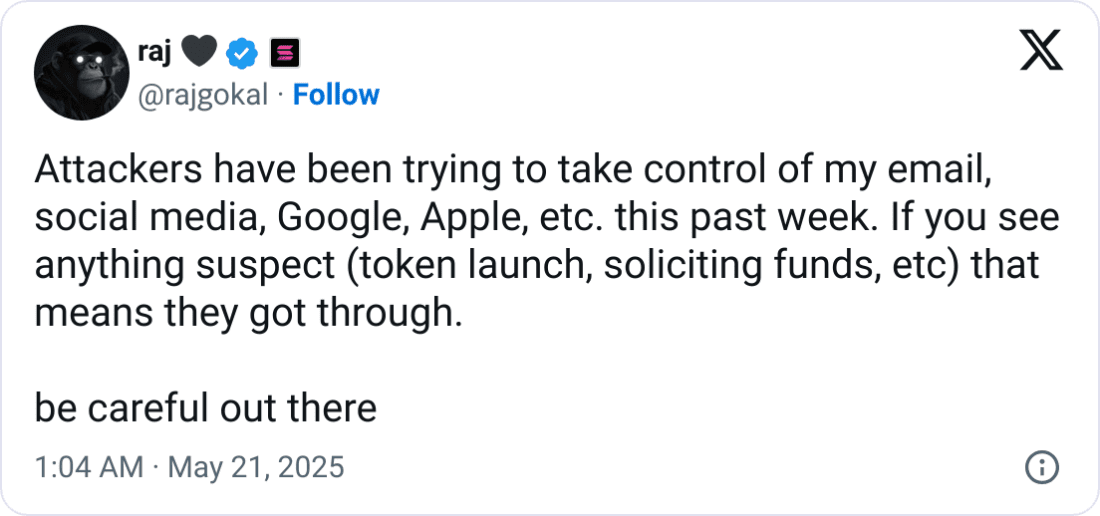
The Solana Foundation and Raj Gokal were contacted for comment but have yet to release an official statement. Prior to the hack, Gokal had posted on X (formerly Twitter) on May 20th, warning followers that attackers had been attempting to compromise his email and social media accounts, urging caution regarding any unusual activity.
Potential Explanations and Concerns:
Several questions arise from this incident:
- Data Breach: Did the hacker obtain the photos through a data breach at a cryptocurrency exchange or other service where Gokal had submitted his KYC information?
- Phishing or Social Engineering: Could Gokal have been a victim of a phishing attack or social engineering scheme that tricked him into revealing his personal information?
- Deepfakes: While unconfirmed, the possibility of AI-generated deepfakes being used to create the images cannot be ruled out. Deepfakes have been used in other extortion attempts within the crypto space.
Deepfakes and Crypto Extortion:
The rise of AI-powered deepfakes poses a growing threat to individuals and organizations. In April, crypto podcaster Scott Melker revealed that scammers had created a fake version of his driver’s license using AI and successfully stolen at least $4 million from a victim. This highlights the potential for deepfakes to be used in identity theft and financial fraud.
KYC Data Security and Privacy:
The incident also raises concerns about the security and privacy of KYC information collected by cryptocurrency exchanges. Coinbase recently faced a lawsuit alleging breaches of Illinois biometric privacy laws, with claims that the exchange failed to properly disclose its use of third-party vendors for ID verification.
Key Takeaways:
- Social Media Security is Critical: Protecting social media accounts with strong passwords and two-factor authentication is crucial to prevent unauthorized access.
- Be Wary of Phishing Attempts: Exercise caution when clicking on links or providing personal information online.
- Demand Transparency from Crypto Exchanges: Users should demand transparency from crypto exchanges regarding how their KYC data is collected, stored, and used.
- The Threat of Deepfakes is Real: The ability to create realistic deepfakes is becoming increasingly sophisticated, making it more difficult to distinguish between real and fake content.
This incident serves as a stark reminder of the vulnerabilities and risks associated with the cryptocurrency ecosystem. It underscores the importance of robust security measures, increased awareness of phishing scams, and the need for greater transparency and accountability in the handling of personal data.