Republican Representative William Timmons is pressing the SEC for transparency regarding its historical perspective on Ethereum, a move that could significantly impact the regulatory landscape for ETH and the broader crypto market.
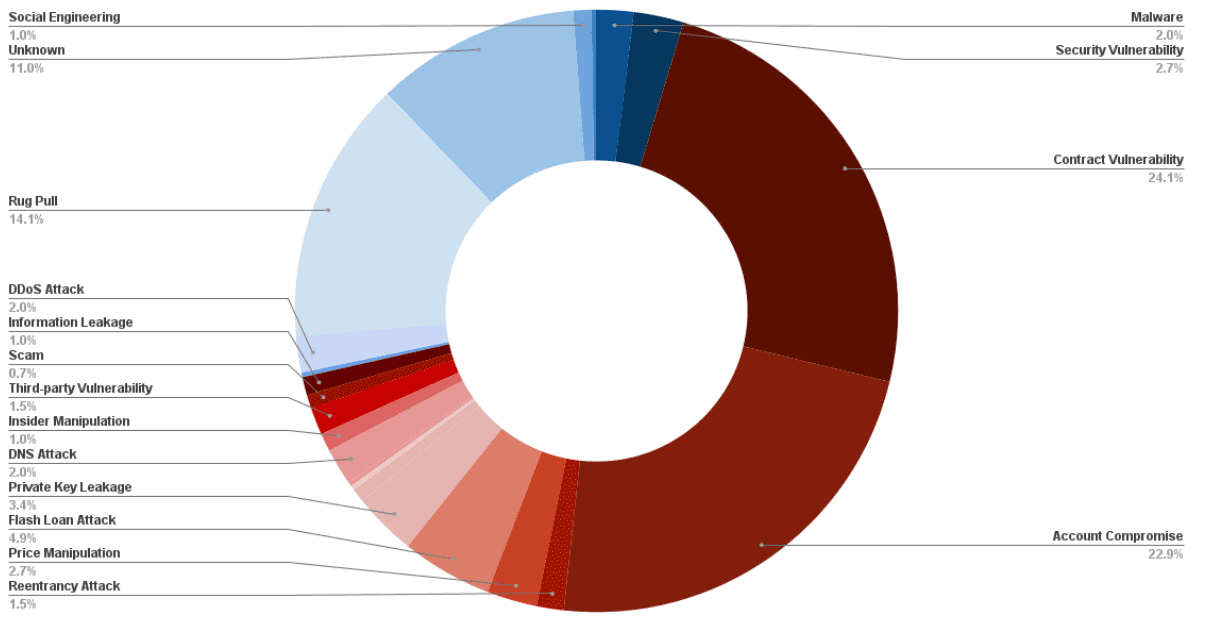
Tag: Cybersecurity
Deepfake Crypto Scams Surge: 87 Rings Busted in Q1 2025
AI-powered deepfakes are becoming a significant tool in crypto scams, with fraudsters impersonating public figures and executives to deceive users. A recent report highlights the alarming increase in these sophisticated schemes.
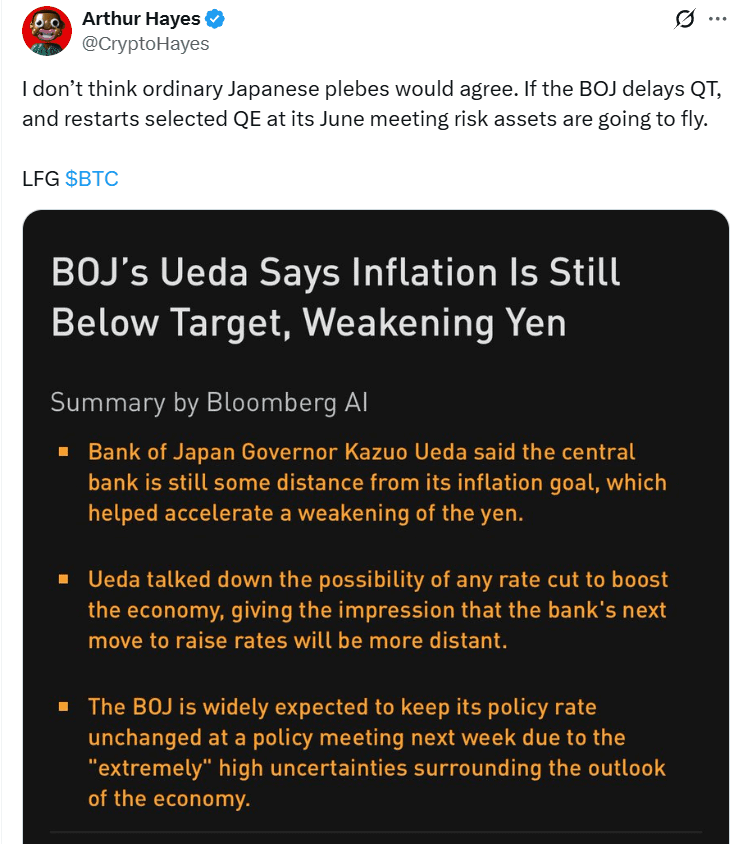
Crypto Market Update: BOJ Meeting, Corporate BTC Buys, and Paraguay’s Bitcoin U-Turn
A look at today’s top crypto news: Arthur Hayes’ prediction of a Bitcoin rally based on the Bank of Japan’s policy meeting, increasing corporate Bitcoin acquisitions, and a denial from Paraguay regarding Bitcoin as legal tender.
US House Committee Advances Crypto Market Structure Bill: What It Means for You
The US House Agriculture Committee passed the Digital Asset Market Clarity (CLARITY) Act, signaling progress in establishing a regulatory framework for digital assets. This article analyzes the potential impact of this development.
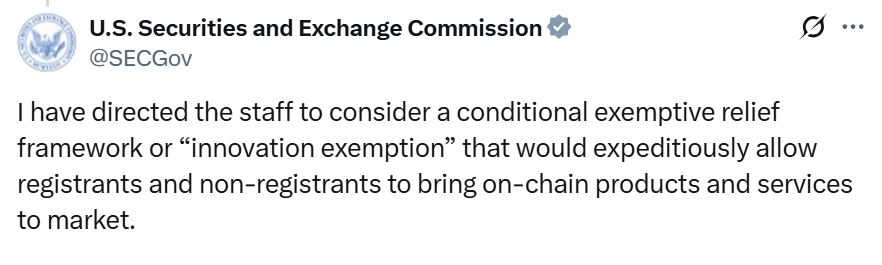
SEC Considers ‘Innovation Exemption’ to Spur Onchain Crypto Development
The SEC is exploring a new exemption framework to encourage crypto innovation, potentially speeding up the launch of onchain products and services. This move signals a shift in the agency’s approach to crypto regulation.